What Type Of Access Control List Can Filter Traffic Based On Port Number Or Protocol Type?
In the reckoner networking world, an ACL is one of the most central components of security.
An Access Control Lists "ACL" is a function that watches incoming and outgoing traffic and compares it with a set of defined statements.
In this article, nosotros will go deep into the functionality of ACLs, and respond the post-obit mutual questions nearly ACLs?
- What is an Access Control List?
- Why Utilize An ACL?
- Where Can Yous Place An ACL?
- What Are The Components of An ACL?
- What Are The Types of ACLs?
- How to Implement An ACL on a Router?
What is an Admission Control List?
Access Control Lists "ACLs" are network traffic filters that can control incoming or outgoing traffic.
ACLs work on a set up of rules that define how to forward or block a parcel at the router'south interface.
An ACL is the same every bit a Stateless Firewall, which only restricts, blocks, or allows the packets that are flowing from source to destination.
When y'all define an ACL on a routing device for a specific interface, all the traffic flowing through will be compared with the ACL statement which volition either cake information technology or let it.
The criteria for defining the ACL rules could exist the source, the destination, a specific protocol, or more than data.
ACLs are mutual in routers or firewalls, but they can likewise configure them in any device that runs in the network, from hosts, network devices, servers, etc.
Why Use An ACL?
The primary idea of using an ACL is to provide security to your network. Without it, whatever traffic is either immune to enter or exit, making it more than vulnerable to unwanted and dangerous traffic.
To improve security with an ACL you can, for instance, deny specific routing updates or provide traffic period control.
Equally shown in the picture beneath, the routing device has an ACL that is denying access to host C into the Fiscal network, and at the same time, it is assuasive access to host D.
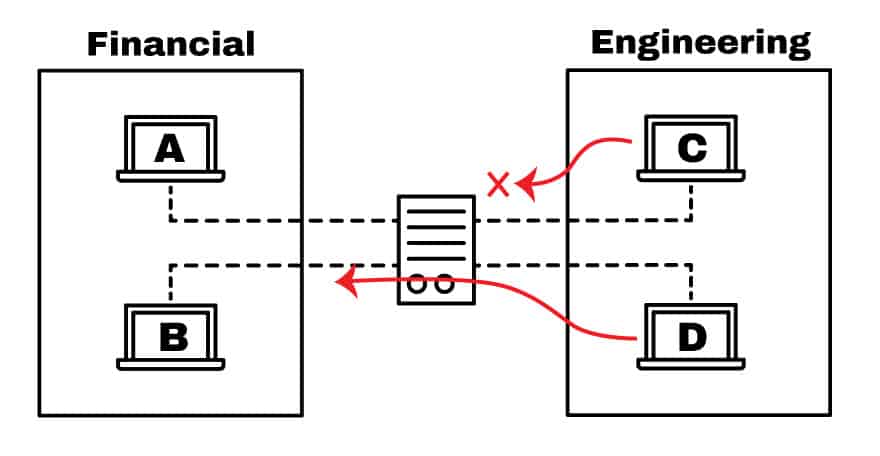
With an ACL you can filter packets for a single or grouping of IP accost or different protocols, such as TCP or UDP.
So for example, instead of blocking only ane host in the engineering team, you lot can deny admission to the unabridged network and simply allow one. Or y'all tin can as well restrict the admission to host C.
If the Engineer from host C, needs to access a spider web server located in the Financial network, you lot can just allow port 80, and cake everything else.
Where Tin You Place An ACL?
The devices that are facing unknown external networks, such as the Cyberspace, need to take a way to filter traffic. And then, one of the all-time places to configure an ACL is on the edge routers.
A routing device with an ACL can be placed facing the Internet and connecting the DMZ (De-Militarized Zone), which is a buffer zone that divides the public Internet and the individual network.
The DMZ is reserved for servers that need admission from the exterior, such as Spider web Servers, app servers, DNS servers, VPNs, etc.
As shown in the moving picture below, the pattern shows a DMZ divided by two devices, ane that separates the trusted zone from the DMZ and another that separates it with the Net (public network).
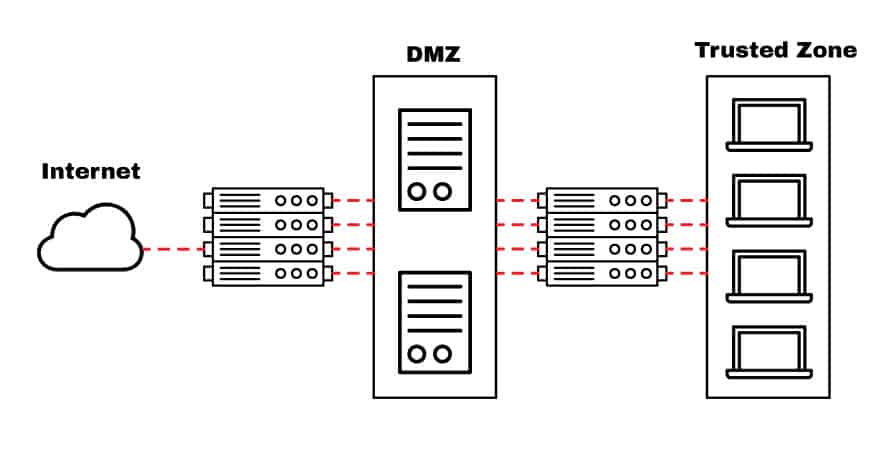
The router facing the Cyberspace acts as a gateway for all exterior networks. Information technology provides general security by blocking larger subnets from going out or in.
You can also configure an ACL in this router to protect against specific well-known ports (TCP or UDP).
The internal router, located between the DMZ and the Trusted Zone, can be configured with more restrictive rules to protect the internal network. Notwithstanding, this is a slap-up place to cull a stateful firewall over an ACL.
Just Why is it Meliorate to place an ACL vs. Stateful Firewall to protect the DMZ?
ACLs are directly configured in a device's forwarding hardware, so they practice not compromise the end operation.
Placing a stateful firewall to protect a DMZ can compromise your network'due south operation.
Choosing an ACL router to protect high-performance assets, such equally applications or servers can exist a better option. While ACLs might not provide the level of security that a stateful firewall offer, they are optimal for endpoints in the network that need high speed and necessary protection.
What Are The Components of An ACL?
The implementation for ACLs is pretty similar in nigh routing platforms, all of which take general guidelines for configuring them.
Remember that an ACL is a set of rules or entries. Y'all can accept an ACL with single or multiple entries, where each i is supposed to do something, information technology tin be to permit everything or cake nothing.
When you define an ACL entry, you'll need necessary information.
- Sequence Number:
Identify an ACL entry using a number. - ACL Proper noun:
Ascertain an ACL entry using a proper noun. Instead of using a sequence of numbers, some routers allow a combination of messages and numbers. - Remark:
Some Routers allow you to add together comments into an ACL, which can assist you to add detailed descriptions. - Statement:
Deny or permit a specific source based on address and wildcard mask. Some routing devices, such equally Cisco, configure an implicit deny argument at the end of each ACL by default. - Network Protocol:
Specify whether deny/allow IP, IPX, ICMP, TCP, UDP, NetBIOS, and more than. - Source or Destination:
Define the Source or Destination target as a Single IP, a Accost Range (CIDR), or all Addresses. - Log:
Some devices are capable of keeping logs when ACL matches are found. - Other Criteria:
Advanced ACLs allow you to utilise command traffic through the Type of Service (ToS), IP precedence, and differentiated services codepoint (DSCP) priority.
What Are The Types of ACLs?
There are four types of ACLs that you tin use for unlike purposes, these are standard, extended, dynamic, reflexive, and fourth dimension-based ACLs.
1. Standard ACL
The standard ACL aims to protect a network using only the source address.
It is the virtually bones blazon and can be used for simple deployments, but unfortunately, it does non provide strong security. The configuration for a standard ACL on a Cisco router is as follows:

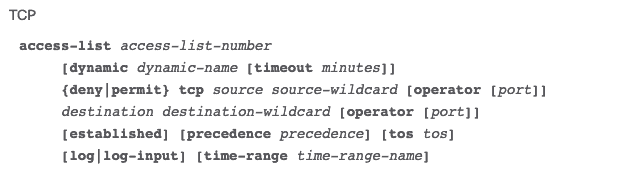
2. Extended ACL
With the extended ACL, you tin also cake source and destination for single hosts or entire networks.
You tin also use an extended ACL to filter traffic based on protocol data (IP, ICMP, TCP, UDP).
The configuration of an extended ACL in a Cisco router for TCP is as follows:
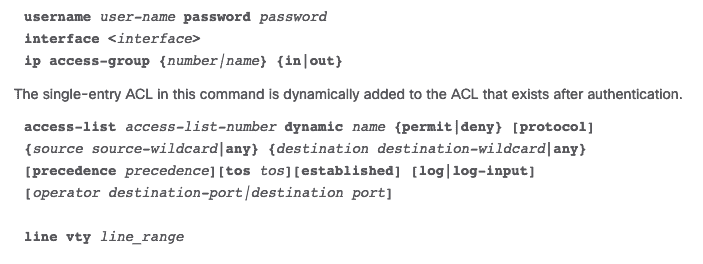
3. Dynamic ACL
Dynamic ACLs, rely upon extended ACLs, Telnet, and authentication. This blazon of ACLs are often referred to as "Lock and Key" and can exist used for specific timeframes.
These lists permit access to a user to a source or destination only if the user authenticates to the device via Telnet.
The following is the configuration of a Dynamic ACL in a Cisco router.
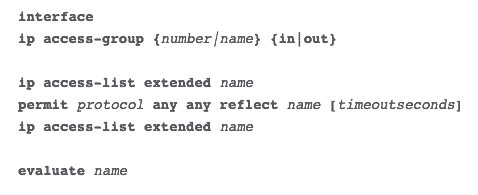
four. Reflexive ACL
Reflexive ACLs are also referred to equally IP session ACLs. These blazon of ACLs, filter traffic based on upper layer session information.
They react to sessions originated inside the router to whether allow outbound traffic or restrict incoming traffic. The router recognizes the outbound ACL traffic and creates a new ACL entry for the inbound.
When the session finishes, the entry is removed.
The configuration of a reflexive ACL in a Cisco router is as follows:
How to Implement An ACL On your Router?
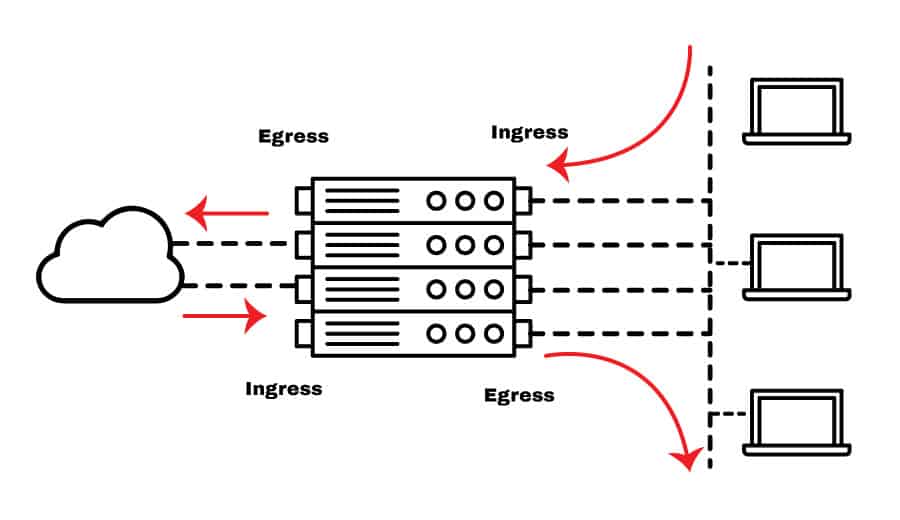
Agreement ingress and egress traffic (or inbound and outbound) in a router, is critical for proper ACL implementation.
When setting rules for an ACL, all traffic flows are based on the point-of-view of the router'southward interface (not the other networks).
As y'all tin can see from the picture below, ingress traffic is the flow coming from a network, whether it is external or internal, into the router's interface. The egress traffic, on the other hand, is the menstruation from the interface going out into a network.
For an ACL to work, apply it to a router's interface. Since all routing and forwarding decisions are made from the router's hardware, the ACL statements tin exist executed much faster.
When you lot create an ACL entry, the source address goes commencement, and the destination goes after. Take the example of the extended ACL configuration for IP on a Cisco Router. When you create a Deny/Let rule, y'all must showtime define the source, and so the destination IP.

The incoming period is the source of all hosts or network, and the outgoing is the destination of all hosts and networks.
What is the Source if yous desire to Block Traffic coming from the Internet?
Remember that inbound traffic is coming from the outside network to your router interface.
So the source is an IP address from the Cyberspace (a web server public IP address) or everything (wildcard mask of 0.0.0.0), and the destination is an internal IP address.
On the contrary, what if you lot what to Cake a Specific Host to connect to the Net?
The inbound traffic is coming from the inside network to your router interface and going out to the Internet. And so the source is the IP from the internal host, and the destination is the IP address on the Internet.
Summary
ACLs are the packet filters of a network.
They can restrict, permit, or deny traffic which is essential for security. An ACL allows you to control the flow of packets for a single or grouping of IP address or different for protocols, such every bit TCP, UDP, ICMP, etc.
Placing an ACL on the wrong interface or mistakenly changing source/destination tin can create a negative touch on on the network. A single ACL statement can leave an entire business concern without the Internet.
To avert negative performance is disquisitional to understand the inbound and outbound traffic flows, how ACLs work, and where to place them. Retrieve that a router'south job is to forrad traffic through the correct interface and so that a flow tin can be either coming information technology (inbound) or going out (outbound).
Although a stateful firewall provides much better security, they can compromise the operation of the network. But an ACLs is deployed right on the interface, and the router uses its hardware capabilities to process it, making it much faster and nonetheless giving a good level of security.
What Type Of Access Control List Can Filter Traffic Based On Port Number Or Protocol Type?,
Source: https://www.ittsystems.com/access-control-list-acl/
Posted by: goodmancrooking1973.blogspot.com


0 Response to "What Type Of Access Control List Can Filter Traffic Based On Port Number Or Protocol Type?"
Post a Comment